It is impossible to pass HP HPE7-A01 exam without any help in the short term. Come to Ucertify soon and find the most advanced, correct and guaranteed HP HPE7-A01 practice questions. You will get a surprising result by our Renewal Aruba Certified Campus Access Professional Exam practice guides.
Check HPE7-A01 free dumps before getting the full version:
NEW QUESTION 1
You are setting up a customer's 15 headless loT devices that do not support 802.1X. What should you use?
- A. Multiple Pre-Shared Keys (MPSK) Local
- B. Clearpass with WPA3-PSK
- C. Clearpass with WPA3-AES
- D. Multiple Pre-Shared Keys (MPSK) with WPA3-AES
Answer: A
Explanation:
MPSK Local is a feature that can be used to set up 15 headless IoT devices that do not support 802.1X authentication. MPSK Local allows the switch to automatically generate and assign unique pre-shared keys for devices based on their MAC addresses, without requiring any configuration on the devices or an external authentication server. The other options are incorrect because they either require 802.1X authentication, which is not supported by the IoT devices, or WPA3 encryption, which is not supported by Aruba CX switches. References: https://www.arubanetworks.com/techdocs/AOS- CX/10.04/HTML/5200-6728/bk01-ch05.html https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01- ch06.html
NEW QUESTION 2
In an ArubaOS 10 architecture using an AP and a gateway, what happens when a client attempts to join the network and the WLAN is configured with OWE?
- A. Authentication information is not exchanged
- B. The Gateway will not respond.
- C. No encryption is applied.
- D. RADIUS protocol is utilized.
Answer: A
Explanation:
This is the correct statement about what happens when a client attempts to join the network and the WLAN is configured with OWE (Opportunistic Wireless Encryption). OWE is a standard that provides encryption for open networks without requiring any authentication or credentials from the client or the network. OWE uses a Diffie-Hellman key exchange mechanism to establish a secure session between the client and the AP without exchanging any authentication information. The other options are incorrect because they either describe scenarios that require authentication or encryption methods that are not used by OWE. References: https://www.arubanetworks.com/assets/wp/WP_WiFi6.pdf https://www.arubanetworks.com/assets/ds/DS_AP510Series.pdf
NEW QUESTION 3
What does the 802.3bz standard describe?
- A. 2.5Gb and 5Gb Ethernet ports
- B. 60 W and 90W PoE
- C. AP directed roaming between APs
- D. 60 GHz P2P Wi-Fi
Answer: A
Explanation:
802.3bz is a standard for Ethernet over twisted pair at speeds of 2.5 and 5 Gbit/s. These use the same cabling as the ubiquitous Gigabit Ethernet, yet offer higher speeds. The resulting standards are named 2.5GBASE-T and 5GBASE-T.
Option A: 2.5Gb and 5Gb Ethernet ports
This is because option A shows how to identify the speed of an Ethernet port based on its name and the standard it supports. A port that supports 2.5GBASE-T or 5GBASE-T is a multi-gigabit port that can operate at speeds of up to 2.5 Gbit/s or 5 Gbit/s over twisted pair cables23.
Therefore, option A is correct.
1: https://en.wikipedia.org/wiki/2.5GBASE-T_and_5GBASE-T 2: https://kb.netgear.com/000049004/What-is-Multi-Gigabit-Ethernet-and-how-can-I-benefit-from-using-NETGEAR-Multi-Gigabit-Ethernet-Switches-in-my-network 3: https://arstechnica.com/gadgets/2016/09/5gbps-ethernet-standard-details-8023bz/
NEW QUESTION 4
What is the best practice for handling voice traffic with dynamic segmentation on AOS-CX switches?
- A. Switch authentication and local forwarding of the voice traffic
- B. Switch authentication and user-based tunneling of the voice traffic.
- C. Central authentication and port-based tunneling of the voice traffic.
- D. Controller authentication and port-based tunneling of all traffic
Answer: A
Explanation:
This is the best practice for handling voice traffic with dynamic segmentation on AOS-CX switches. Dynamic segmentation is a feature that allows AOS-CX switches to tunnel user traffic to a controller or another switch based on user roles and policies. For voice traffic, it is recommended to use switch authentication and local forwarding, which means the voice devices are authenticated by the switch and their traffic is forwarded locally without tunneling. This reduces latency and jitter for voice traffic and improves voice quality. The other options are incorrect because they either use central authentication or tunneling, which are not optimal for voice traffic. References: https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01- ch05.html https://www.arubanetworks.com/assets/ds/DS_AOS-CX.pdf
NEW QUESTION 5
Which statement best describes QoS?
- A. Determining which traffic passes specified quality metrics
- B. Scoring traffic based on the quality of the contents
- C. Identifying specific traffic for special treatment
- D. Identifying the quality of the connection
Answer: A
Explanation:
QoS stands for Quality of Service and is a mechanism that allows network devices to prioritize and differentiate traffic based on certain criteria, such as application type, source, destination, etc3. QoS involves identifying specific traffic for special treatment and applying policies and actions to improve its performance or meet certain service level agreements (SLAs)3. QoS can help network devices to manage congestion, delay, jitter, packet loss, bandwidth allocation, etc., for different types of traffic3. QoS can be implemented at various layers of the network stack and across different network domains. References: 3 https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/qos/configuration/15-mt/qos-15-mt-book/qos-overview.html
NEW QUESTION 6
Your customer currently has Iwo (2) 5406 modular switches with MSTP configured as their core switches. You are proposing a new solution. What would you explain regarding the Aruba CX VSX switch pair when the Primary VSX node is replaced and the system MAC is replaced?
- A. VSX will select the MAC address from a node that is the lower ID.
- B. Configure vMAC on the Primary VSX node under VSX to retain MAC after hardware replacement.
- C. VSX will select the MAC address from a node that is a higher ID.
- D. During the initial VSX configuration, the system-mac is assigned with a fixed MAC based on VSX ID.
Answer: D
Explanation:
The system-mac command is used to configure a fixed MAC address for the VSX system. This MAC address is used as the source MAC address for all routed traffic from the VSX node. The system-mac command is highly recommended for preventing traffic disruptions when the primary VSX switch restores after the secondary VSX switch, such as during a primary switch hardware replacement or a power outage2. During the initial VSX configuration, the system-mac is assigned with a fixed MAC based on VSX ID. The system- mac command can be used to change this default MAC address if needed2. Therefore, answer D is correct.
References: 1: Aruba Campus Access documents and learning resources 2: system-mac - Aruba
NEW QUESTION 7
When setting up an Aruba CX VSX pair, which information does the Inter-Switch Link Protocol configuration use in the configuration created?
- A. hello interval is disabled by default
- B. hello interval is based on the value set by dead interval
- C. hello interval 100ms by default
- D. hello interval is 1s by default
Answer: D
Explanation:
The reason is that the Inter-Switch Link Protocol (ISLP) is a protocol that enables VSX stack join and synchronization between two VSX peer switches. ISLP uses a hello interval to exchange control messages between the switches.
The hello interval is a parameter that specifies the time interval between sending hello messages. The default value of the hello interval is 1 second. The hello interval can be configured from 1 second to 10 seconds. https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/index.html
NEW QUESTION 8
How is Multicast Transmission Optimization implemented in an HPE Aruba wireless network?
- A. "The optimal rate for sending multicast frames is based on the highest broadcast rate across all associated clients
- B. When this option is enabled the minimum default rate for multicast traffic is set to 12 Mbps for 5 GHz
- C. The optimal rate for sending multicast frames is based on the lowest broadcast rate across all associated clients.
- D. The optimal rate for sending multicast frames is based on the lowest unicast rate across all associated clients.
Answer: D
Explanation:
multicast transmission optimization is a feature that allows the IAP to select the optimal rate for sending broadcast and multicast frames based on the lowest of unicast rates across all associated clients1. When this option is enabled, multicast traffic can be sent at up to 24 Mbps. The default rate for sending frames for 2.4 GHz is 1 Mbps and 5.0 GHz is 6 Mbps. This option is disabled by default1.
NEW QUESTION 9
When setting up an Aruba CX VSX pair, which information does the Inter-Switch Link Protocol configuration use in the configuration created?
- A. QSVI
- B. MAC tables
- C. UDLD
- D. RPVST+
Answer: B
Explanation:
The information that the Inter-Switch Link Protocol configuration uses in the configuration created is B. MAC tables.
The Inter-Switch Link Protocol (ISL) is a protocol that enables the synchronization of data and state information between two VSX peer switches. The ISL uses a version control mechanism and provides backward compatibility regarding VSX synchronization capabilities. The ISL can span long distances (transceiver dependent) and supports different speeds, such as 10G, 25G, 40G, or 100G1.
One of the data components that the ISL synchronizes is the MAC table, which is a database that stores the MAC addresses of the devices connected to the switch and the corresponding ports or VLANs. The ISL ensures that both VSX peers have the same MAC table entries and can forward traffic to the correct destination2. The ISL also synchronizes other data components, such as ARP table, LACP states for VSX LAGs, and MSTP states2.
NEW QUESTION 10
DRAG DROP
Match the topics with the underlying technologies (Options may be used more than once or not at all.)
Solution:
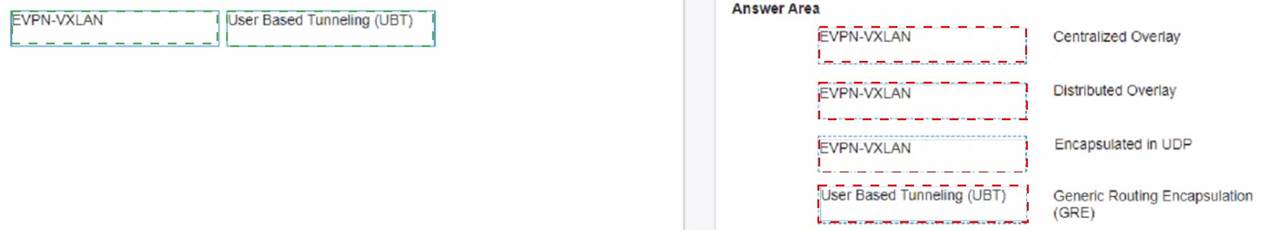
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 11
A customer is using Aruba Cloud Guest, but visitors keep complaining that the captive portal page keeps coming up after devices go to sleep Which solution should be enabled to deal with this issue?
- A. MAC Caching under the splash page
- B. MAC Caching under the user-role
- C. Wireless Caching under the splash page
- D. MAC Caching under the WLAN
Answer: A
Explanation:
MAC Caching is a feature that allows a guest user to bypass the captive portal page after the first authentication based on their MAC address1 MAC Caching can be enabled under the splash page settings in Aruba Cloud Guest2 MAC Caching can improve the user experience and reduce the network overhead by eliminating the need for repeated authentication.
NEW QUESTION 12
What steps are part of the Key Management workflow when a wireless device is roaming from AP1 to AP2? (Select two.)
- A. AP1 will cache the client's information and send it to the Key Management service
- B. The Key Management service receives from AirMatch a list of all AP2's neighbors
- C. The Key Management service receives a list of all AP1 s neighbors from AirMatch.
- D. The Key Management service then generates R1 keys for AP2's neighbors.
- E. A client associates and authenticates with the AP2 after roaming from AP1
Answer: AD
Explanation:
The correct steps that are part of the Key Management workflow when a wireless device is roaming from AP1 to AP2 are A and D.
* A. AP1 will cache the client??s information and send it to the Key Management service. This is true because when a client associates and authenticates with AP1, AP1 will generate a pairwise master key (PMK) for the client and store it in its cache. AP1 will also send the PMK and other client information, such as MAC address, VLAN, and SSID, to the Key Management service, which is a centralized service that runs on Aruba Mobility Controllers (MCs) or Mobility Master (MM) devices1. The Key Management service will use this information to facilitate fast roaming for the client.
* D. The Key Management service then generates R1 keys for AP2??s neighbors. This is true because when the Key Management service receives the client information from AP1, it will use the PMK to derive R0 and R1 keys for the client. R0 keys are used to generate R1 keys, which are used to generate pairwise transient keys (PTKs) for encryption. The Key Management service will distribute the R1 keys to AP2 and its neighboring APs, which are determined by AirMatch based on RF proximity2. This way, when the client roams to AP2 or any of its neighbors, it can skip the 802.1X authentication and use the R1 key to quickly generate a PTK with the new AP3.
* B. The Key Management service receives from AirMatch a list of all AP2??s neighbors. This is false because the Key Management service does not receive this information from AirMatch directly. AirMatch is a feature that runs on MCs or MM devices and optimizes the RF performance of Aruba devices by using machine learning algorithms. AirMatch periodically sends neighbor reports to all APs, which contain information about their nearby APs based on signal strength and interference. The APs then send these reports to the Key Management service, which uses them to determine which APs should receive R1 keys for a given client2.
* C. The Key Management service receives a list of all AP1 s neighbors from AirMatch. This is false for the same reason as B. The Key Management service does not receive this information from AirMatch directly, but from the APs that send their neighbor reports.
* E. A client associates and authenticates with the AP2 after roaming from AP1. This is false because a client does not need to authenticate with AP2 after roaming from AP1 if it has already authenticated with AP1 and received R1 keys from the Key Management service. The client only needs to associate with AP2 and perform a four-way handshake using the R1 key to generate a PTK for encryption3. This is called fast roaming or 802.11r roaming, and it reduces the latency and disruption caused by full authentication.
1: ArubaOS 8.7 User Guide 2: ArubaOS 8.7 User Guide 3: ArubaOS 8.7 User Guide : ArubaOS 8.7 User Guide
NEW QUESTION 13
A company recently upgraded its campus switching infrastructure with Aruba 6300 CX switches. They have implemented 802.1X authentication on edge ports where laptop and loT devices typically connect An administrator has noticed that for PoE devices the pons are delivering the maximum wattage instead of what the device actually needs Upon connecting the loT devices, the devices request their specific required wattage through information exchange
- A. Concerned about this waste of electricity, what should the administrator implement to solve this problem?
- B. Enable AAA authentication to exempt LLDP and/or CDP information
- C. Globally enable the QoS trust setting for LLDP and/or CDP
- D. Create device profiles with the correct power definitions.
- E. implement a classifier policy with the correct power definitions.
Answer: D
Explanation:
According to the Aruba Documentation Portal1, the Aruba 6300 CX switches support various features to control the PoE devices on specific ports, such as device profiles and classifier policies. These features can help reduce the power consumption and improve the performance of the PoE devices.
1: https://www.arubanetworks.com/techdocs/AOS-CX/10.10/HTML/monitoring_6300-6400/Content/Chp_LEDs/fro-pan-led-630.htm 2:
https://www.arubanetworks.com/products/switches/6300-series/ 3: https://docs.samsungknox.com/admin/knox-manage/configure/profile/configure-profile-policies/configure-profile-policies-by-device-platform/
NEW QUESTION 14
With Aruba CX 6300. how do you configure ip address 10 10 10 1 for the interface in default state for interface 1/1/1?
- A. int 1/1/1. switching, ip address 10 10 10 1/24
- B. int 1/1/1. no switching, ip address 10 10 10.1/24
- C. int 1/1/1. ip address 10.10.10.1/24
- D. int 1/1/1. routing, ip address 10.10.10 1/24
Answer: B
Explanation:
To configure an IP address for an interface in default state for interface 1/1/1 on Aruba CX 6300 switch, you need to disable switching on the interface first with the command no switching. Then you can assign an IP address with the command ip address. The other options are incorrect because they either do not disable switching or use invalid keywords such as switching or routing. References: https://www.arubanetworks.com/techdocs/AOS-CX_10_08/UG/bk01-ch01.html https://www.arubanetworks.com/techdocs/AOS-CX_10_08/UG/bk01-ch02.html
NEW QUESTION 15
You need to create a keepalive network between two Aruba CX 8325 switches for VSX configuration How should you establish the keepalive connection?
- A. SVI, VLAN trunk allowed all on ISL in default VRF
- B. routed port in custom VRF
- C. loopback 0 and OSPF area 0 in default VRF
- D. SVI, VLAN trunk allowed all on ISL in custom VRF
Answer: B
Explanation:
To establish a keepalive connection between two Aruba CX 8325 switches for VSX configuration, you need to use a routed port in custom VRF. A routed port is a physical port that acts as a layer 3 interface and does not belong to any VLAN. A custom VRF is a virtual routing and forwarding instance that provides logical separation of routing tables. By using a routed port in custom VRF, you can isolate the keepalive traffic from other traffic and prevent routing loops or conflicts. The other options are incorrect because they either do not use a routed port or do not use a custom VRF. References: https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200-6728/bk01- ch07.html https://www.arubanetworks.com/techdocs/AOS-CX/10.04/HTML/5200- 6728/bk01-ch02.html
NEW QUESTION 16
Refer to Exhibit: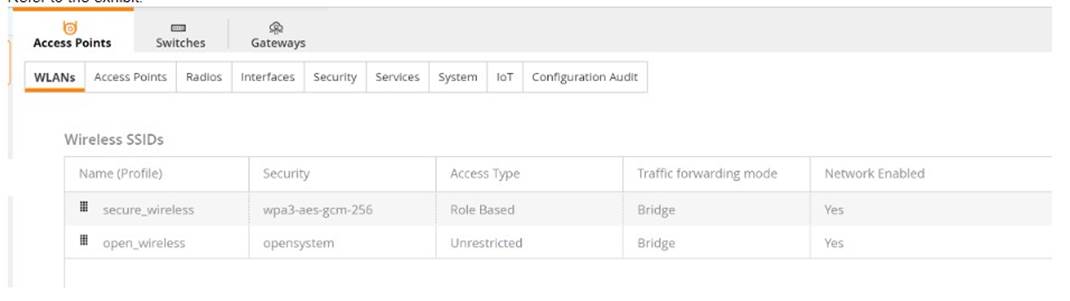
A company has deployed 200 AP-635 access points. To take advantage of the 6 GHz band, the administrator has attempted to configure a new WPA3-OWE SSID in Central but is not working as expected.
What would be the correct action to fix the issue?
- A. Change the SSID to WPA3-Enterprise (CNSA).
- B. Change the SSID to WPA3-Personal.
- C. Change the SSID to WPA3-Enhanced Open.
- D. Change the SSID to WPA3-Enterprise (CCM).
Answer: C
Explanation:
The correct action to fix the issue is C. Change the SSID to WPA3-Enhanced Open.
WPA3-OWE is not a valid SSID type in Central. OWE stands for Opportunistic Wireless Encryption, and it is a feature that provides encryption for open networks without requiring authentication. OWE is also known as Enhanced Open, and it is one of the options for WPA3 SSIDs in Central1.
According to the Aruba document Configuring WLAN Settings for an SSID Profile, one of the steps to configure a WPA3 SSID is:
✑ Select the Security Level from the drop-down list. The following options are available:
The other options are incorrect because:
✑ A. WPA3-Enterprise (CNSA) is a valid SSID type, but it requires 802.1X authentication with a RADIUS server, which may not be suitable for the company??s use case.
✑ B. WPA3-Personal is a valid SSID type, but it requires a passphrase to join the network, which may not be suitable for the company??s use case.
✑ D. WPA3-Enterprise (CCM) is a valid SSID type, but it requires 802.1X authentication with a RADIUS server, which may not be suitable for the company??s use case.
NEW QUESTION 17
DRAG DROP
Match the terms below to their characteristics (Options may be used more than once or not at all.)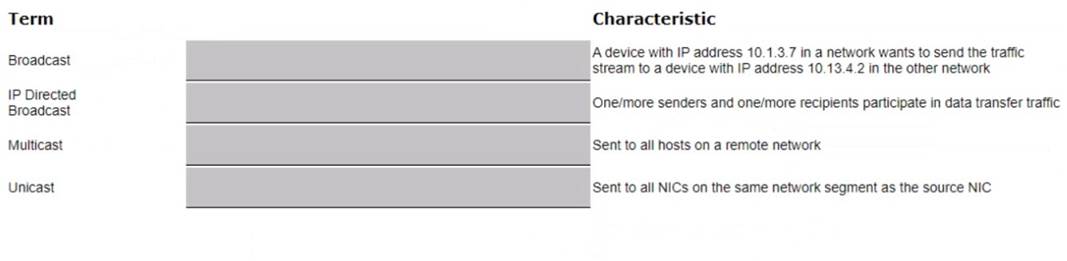
Solution:
a) A device with IP address 10.1.3.7 in a network wants to send the traffic stream to a device with IP address 10.13.4.2 in the other network -> Unicast
b) One/more senders and one/more recipients participate in data transfer traffic ->
Multicast
c) Sent to all hosts on a remote network -> IP Directed Broadcast
d) Sent to all NICs on the same network segment as the source NIC -> Broadcast
References: 1 https://www.thestudygenius.com/unicast-broadcast-multicast/
The terms broadcast, IP directed broadcast, multicast, and unicast are different types of communication or data transmission over a network. They differ in how many devices are involved in the communication and how they address the messages. The following table summarizes the characteristics of each term1:
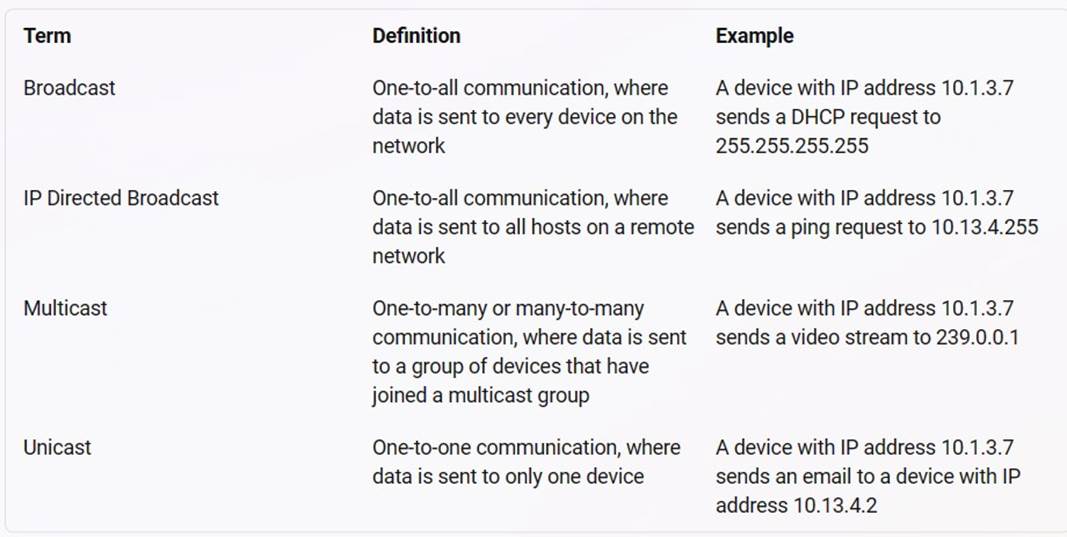
Does this meet the goal?
- A. Yes
- B. Not Mastered
Answer: A
NEW QUESTION 18
What is enabled by LLDP-MED? (Select two.)
- A. Voice VLANs can be automatically configured for VoIP phones
- B. APs can request power as needed from PoE-enabled switch ports
- C. iSCSl client devices can request to have flow control enabled
- D. GVRP VLAN information can be used to dynamically add VLANs to a trunk
- E. iSCSl client devices can set the required MTU setting for the port.
Answer: AB
Explanation:
These are two benefits enabled by LLDP-MED (Link Layer Discovery Protocol - Media Endpoint Discovery). LLDP-MED is an extension of LLDP that provides additional capabilities for network devices such as VoIP phones and APs. One of the capabilities is to automatically configure voice VLANs for VoIP phones, which allows them to be placed in a separate VLAN from data devices and receive QoS and security policies. Another capability is to request power as needed from PoE-enabled switch ports, which allows APs to adjust their power consumption and performance based on the available power budget. The other options are incorrect because they are either not enabled by LLDP-MED or not related to LLDP-MED. References: https://www.arubanetworks.com/techdocs/ArubaOS_86_Web_Help/Content/arubaos-solutions/wlan-qos/lldp-med.htm
https://www.arubanetworks.com/techdocs/ArubaOS_86_Web_Help/Content/arubaos-solutions/wlan-rf/poe.htm
NEW QUESTION 19
Which method is used to onboard a new UXI in an existing environment with 802 1X authentication? (The sensor has no cellular connection)
- A. Use the UXI app on your smartphone and connect the UXI via Bluetooth
- B. Use the Aruba installer app on your smartphone to scan the barcode
- C. Connect the new UXI from an already installed one and adjust the initial configuration.
- D. Use the CLI via the serial cable and adjust the initial configuration.
Answer: A
Explanation:
To onboard a new UXI in an existing environment with 802.1X authentication, you need to use the UXI app on your smartphone and connect the UXI via Bluetooth. The UXI app allows you to scan the QR code on the UXI sensor and configure its network settings, such as SSID, password, IP address, etc. The Bluetooth connection allows you to communicate with the UXI sensor without requiring any network access or cellular connection. The other options are incorrect because they either do not use the UXI app or do not use Bluetooth. References: https://www.arubanetworks.com/products/network-management-operations/analytics-monitoring/user-experience-insight-sensors/ https://help.centralon-prem.arubanetworks.com/2.5.4/documentation/online_help/content/nms-on-prem/aos- cx/get-started/uxi-sensor.htm
NEW QUESTION 20
You are working on a network where the customer has a dedicated router with redundant Internet connections Tor outbound high-importance real-time audio streams from their datacenter All of this traffic.
• originates from a single subnet
• uses a unique range of UDP ports
• is required to be routed to the dedicated router
All other traffic should route normally The SVI for the subnet containing the servers originating the traffic is located on the core routing switch in the datacenter What should be configured?
- A. Configure a new OSPF area including both the core routing switch and the dedicated router
- B. Configure a BGP link between the core routing switch and the dedicated router and route filtering.
- C. Configure Policy Based Routing (PBR) on the core routing switch for the VRF with the servers?? SVI
- D. Configure a dedicated VRF on the core routing switch and make the dedicated router the default route.
Answer: C
Explanation:
The reason is that PBR allows you to route packets based on policies that match certain criteria, such as source or destination IP addresses, ports, protocols, etc. PBR can also be used to set metrics, next-hop addresses, or tag traffic for different routes.
NEW QUESTION 21
......
Thanks for reading the newest HPE7-A01 exam dumps! We recommend you to try the PREMIUM 2passeasy HPE7-A01 dumps in VCE and PDF here: https://www.2passeasy.com/dumps/HPE7-A01/ (119 Q&As Dumps)