Exam Code: PCNSE (Practice Exam Latest Test Questions VCE PDF)
Exam Name: Palo Alto Networks Certified Security Engineer (PCNSE)PAN-OS 8.0
Certification Provider: Paloalto-Networks
Free Today! Guaranteed Training- Pass PCNSE Exam.
Online Paloalto-Networks PCNSE free dumps demo Below:
NEW QUESTION 1
Which three steps will reduce the CPU utilization on the management plane? (Choose three.)
- A. Disable SNMP on the management interface.
- B. Application override of SSL application.
- C. Disable logging at session start in Security policies.
- D. Disable predefined reports.E.Reduce the traffic being decrypted by the firewall.
Answer: CDE
NEW QUESTION 2
Which option is an IPv6 routing protocol?
- A. RIPv3
- B. OSPFv3
- C. OSPv3
- D. BGP NG
Answer: B
NEW QUESTION 3
People are having intermittent quality issues during a live meeting via web application.
- A. Use QoS profile to define QoS Classes
- B. Use QoS Classes to define QoS Profile
- C. Use QoS Profile to define QoS Classes and a QoS Policy
- D. Use QoS Classes to define QoS Profile and a QoS Policy
Answer: C
NEW QUESTION 4
What are the differences between using a service versus using an application for Security Policy match?
- A. Use of a "service" enables the firewall to take action after enough packets allow for App-IDidentification
- B. Use of a "service" enables the firewall to take immediate action with the first observed packet based on port numbers Use ofan "application" allows the firewall to take action after enough packets allow for App-ID identification regardless of the portsbeing used.
- C. There are no differences between "service" or "application” Use of an "application" simplifies configuration by allowing use ofa friendly application name instead of port numbers.
- D. Use of a "service" enables the firewall to take immediate action with the first observed packet based on port number
- E. Use ofan "application" allows the firewall to take immediate action it the port being used is a member of the application standardport list
Answer: B
NEW QUESTION 5
Which three options are available when creating a security profile? (Choose three)
- A. Anti-Malware
- B. File Blocking
- C. Url Filtering
- D. IDS/ISP
- E. Threat Prevention
- F. Antivirus
Answer: ABF
NEW QUESTION 6
A critical US-CERT notification is published regarding a newly discovered botnet. The malware is very evasive and is not reliably detected by endpoint antivirus software. Furthermore, SSL is used to tunnel malicious traffic to command-and-control servers on the internet and SSL Forward Proxy Decryption is not enabled.
Which component once enabled on a perirneter firewall will allow the identification of existing infected hosts in an environment?
- A. Anti-Spyware profiles applied outbound security policies with DNS Query action set to sinkhole
- B. File Blocking profiles applied to outbound security policies with action set to alert
- C. Vulnerability Protection profiles applied to outbound security policies with action set to block
- D. Antivirus profiles applied to outbound security policies with action set to alert
Answer: A
NEW QUESTION 7
An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home and experiencing issues completing the connection. the following is the output from the command:
What could be the cause of this problem?
- A. The dead peer detection settings do not match between the Palo Alto Networks Firewall and the ASA.
- B. The Proxy IDs on the Palo Alto Networks Firewall do not match the setting on the ASA.
- C. The public IP addresses do not match for both the Palo Alto Networks Firewall and the ASA.
- D. The shared secrets do not match between the Palo Alto Networks Firewall and the ASA.
Answer: C
NEW QUESTION 8
How would an administrator monitor/capture traffic on the management interface of the Palo Alto Networks NGFW?
- A. Use the debug dataplane packet-diag set capture stage firewall file command.
- B. Enable all four stages of traffic capture (TX, RX, DROP, Firewall).
- C. Use the debug dataplane packet-diag set capture stage management file command.
- D. Use the tcpdump command.
Answer: D
Explanation:
Reference: https://live.paloaltonetworks.com/t5/Learning-Articles/How-to-Run-a-Packet-Capture/ta-p/62390
NEW QUESTION 9
Which three rule types are available when defining policies in Panorama? (Choose three.)
- A. Pre Rules
- B. Post Rules
- C. Default Rules
- D. Stealth Rules
- E. Clean Up Rules
Answer: ABC
Explanation:
https://www.paloaltonetwoHYPERLINK "https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/panorama- web-interface/defining-policies-on-panorama"rks.com/documentation/71/pan-os/web-
interHYPERLINK "https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface- help/panorama-web-interface/defining-policies-on-panorama"face-help/panorama-web- interface/defining-policies-on-panorama
NEW QUESTION 10
What will be the source address in the ICMP packet?
- A. 10.30.0.93
- B. 10.46.72.93
- C. 10.46.64.94
- D. 192.168.93.1
Answer: C
NEW QUESTION 11
A company hosts a publically accessible web server behind a Palo Alto Networks next generation firewall with the following configuration information.
Users outside the company are in the "Untrust-L3" zone The web server physically resides in the "Trust-L3" zone. Web server public IP address: 23.54.6.10
Web server private IP address: 192.168.1.10
Which two items must be NAT policy contain to allow users in the untrust-L3 zone to access the web server? (Choose two)
- A. Untrust-L3 for both Source and Destination zone
- B. Destination IP of 192.168.1.10
- C. Untrust-L3 for Source Zone and Trust-L3 for Destination Zone
- D. Destination IP of 23.54.6.10
Answer: CD
NEW QUESTION 12
Which option is part of the content inspection process?
- A. Packet forwarding process
- B. SSL Proxy re-encrypt
- C. IPsec tunnel encryption
- D. Packet egress process
Answer: A
NEW QUESTION 13
A firewall administrator has completed most of the steps required to provision a standalone Palo Alto Networks Next-Generation Firewall. As a final step, the administrator wants to test one of the security policies.
Which CLI command syntax will display the rule that matches the test?
- A. test security -policy- match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number
- B. show security rule source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>
- C. test security rule source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>
- D. show security-policy-match source <ip_address> destination <IP_address> destination port <port number> protocol <protocol number>test security-policy-match source
Answer: A
Explanation:
test security-policy-match source <source IP> destination <destination IP> protocol <protocol number>
https://live.paloaltonetworks.com/t5/Management-Articles/How-to-Test-Which-Security-Policy- Applies-to-a-Traffic-Flow/ta-p/53693
NEW QUESTION 14
What are three valid method of user mapping? (Choose three)
- A. Syslog
- B. XML API
- C. 802.1X
- D. WildFire
- E. Server Monitoring
Answer: ABE
NEW QUESTION 15
In the following image from Panorama, why are some values shown in red?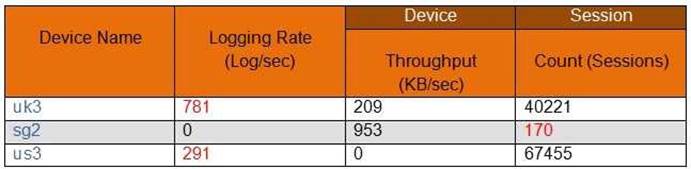
- A. sg2 session count is the lowest compared to the other managed devices.
- B. us3 has a logging rate that deviates from the administrator-configured thresholds.
- C. uk3 has a logging rate that deviates from the seven-day calculated baseline.
- D. sg2 has misconfigured session thresholds.
Answer: C
NEW QUESTION 16
View the GlobalProtect configuration screen capture.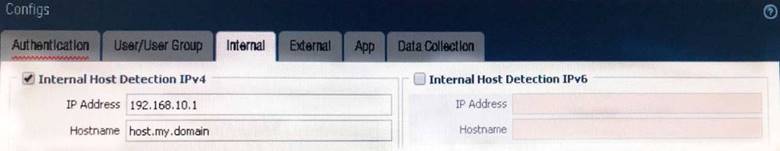
What is the purpose of this configuration?
- A. It configures the tunnel address of all internal clients to an IP address range starting at 192.168.10.1.
- B. It forces an internal client to connect to an internal gateway at IP address 192.168.10.1.
- C. It enables a client to perform a reverse DNS lookup on 192.168.10.1 to detect that it is an internal client.
- D. It forces the firewall to perform a dynamic DNS update, which adds the internal gateway’s hostname and IP address to the DNS server.
Answer: C
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/80/globalprotect/globalprotect-admin-guide/globalprotect-portals/define-the-globalprotect-client-authentication-configurations/define-the-globalprotect-agent-configurations
NEW QUESTION 17
Which PAN-OS® policy must you configure to force a user to provide additional credentials before he is allowed to access an internal application that contains highly-sensitive business data?
- A. Security policy
- B. Decryption policy
- C. Authentication policy
- D. Application Override policy
Answer: C
NEW QUESTION 18
An administrator has been asked to create 100 virtual firewalls in a local, on-premise lab environment (not in “the cloud”). Bootstrapping is the most expedient way to perform this task. Which option describes deployment of a bootstrap package in an on-premise virtual environment?
- A. Use config-drive on a USB stick.
- B. Use an S3 bucket with an ISO.
- C. Create and attach a virtual hard disk (VHD).
- D. Use a virtual CD-ROM with an ISO.
Answer: D
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/newfeaturesguide/management-features/bootstrapping-firewalls-for-rapid-deployment.html
NEW QUESTION 19
Which three log-forwarding destinations require a server profile to be configured? (Choose three)
- A. SNMP Trap
- B. Email
- C. RADIUS
- D. Kerberos
- E. Panorama
- F. Syslog
Answer: ABF
NEW QUESTION 20
Which two options are required on an M-100 appliance to configure it as a Log Collector? (Choose two)
- A. From the Panorama tab of the Panorama GUI select Log Collector mode and then commit changes
- B. Enter the command request system system-mode logger then enter Y to confirm the change to Log Collector mode.
- C. From the Device tab of the Panorama GUI select Log Collector mode and then commit changes.
- D. Enter the command logger-mode enable the enter Y to confirm the change to Log Collector mode.
- E. Log in the Panorama CLI of the dedicated Log Collector
Answer: BE
Explanation:
(https://www.paloaltonetworks.com/documentation/60/panorama/panorama_adminguide/set-up-panorama/set-up-the-m-100-appliance)
NEW QUESTION 21
How are IPV6 DNS queries configured to user interface ethernet1/3?
- A. Network > Virtual Router > DNS Interface
- B. Objects > CustomerObjects > DNS
- C. Network > Interface Mgrnt
- D. Device > Setup > Services > Service Route Configuration
Answer: D
NEW QUESTION 22
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against worms and trojans. Which Security Profile type will protect against worms and trojans?
- A. Anti-Spyware
- B. WildFire
- C. Vulnerability Protection
- D. Antivirus
Answer: A
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/policy/antivirus- profiles
NEW QUESTION 23
Site-A and Site-B need to use IKEv2 to establish a VPN connection. Site A connects directly to the internet using a public IP address. Site-B uses a private IP address behind an ISP router to connect to the internet.
How should NAT Traversal be implemented for the VPN connection to be established between Site-A and Site-B?
- A. Enable on Site-A only
- B. Enable on Site-B only
- C. Enable on Site-B only with passive mode
- D. Enable on Site-A and Site-B
Answer: D
NEW QUESTION 24
Which three split tunnel methods are supported by a globalProtect gateway? (Choose three.)
- A. video streaming application
- B. Client Application Process
- C. Destination Domain
- D. Source Domain
- E. Destination user/group
- F. URL Category
Answer: ABC
NEW QUESTION 25
Which Device Group option is assigned by default in Panorama whenever a new device group is created to manage a Firewall?
- A. Master
- B. Universal
- C. Shared
- D. Global
Answer: C
NEW QUESTION 26
Refer to the exhibit.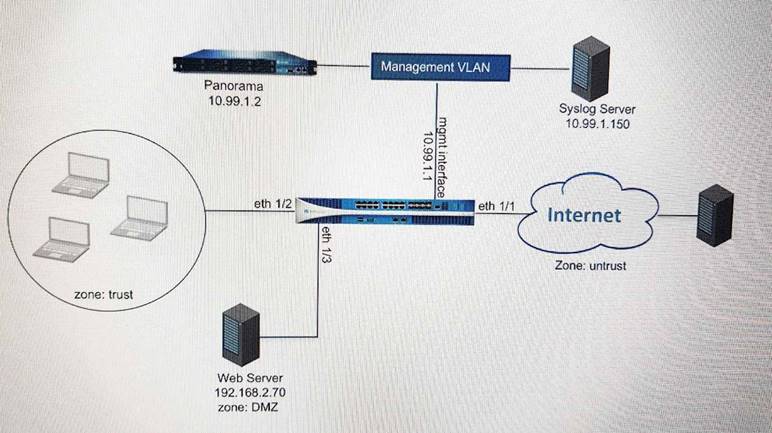
An administrator cannot see any of the Traffic logs from the Palo Alto Networks NGFW on Panorama. The configuration problem seems to be on the firewall side. Where is the best place on the Palo Alto Networks NGFW to check whether the configuration is correct?
A)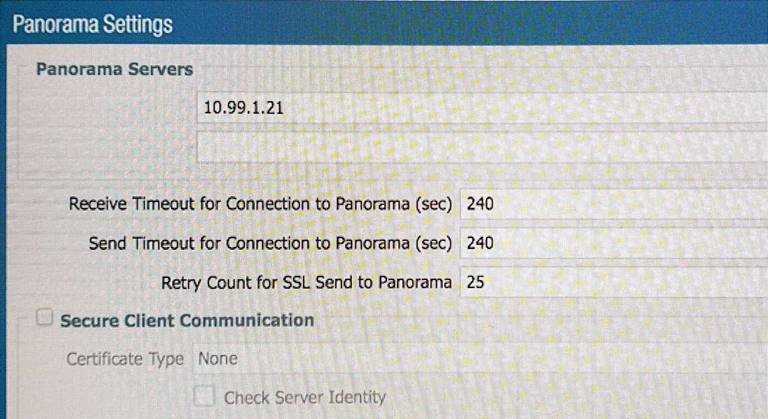
B)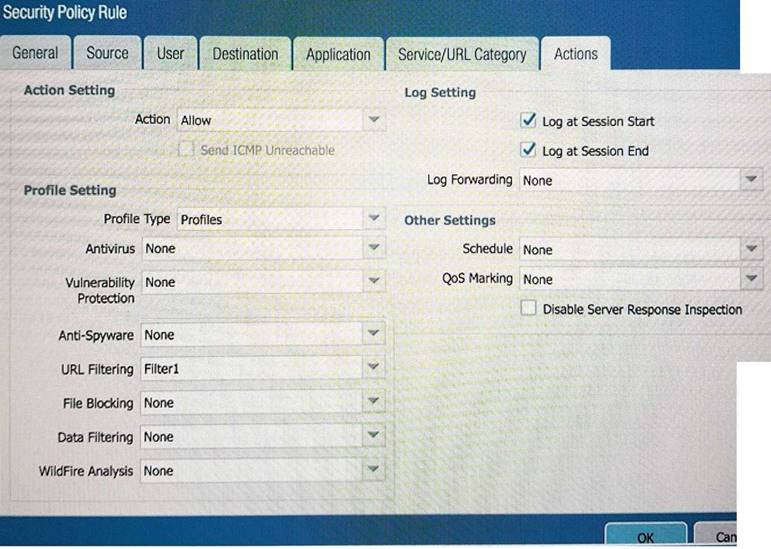
C)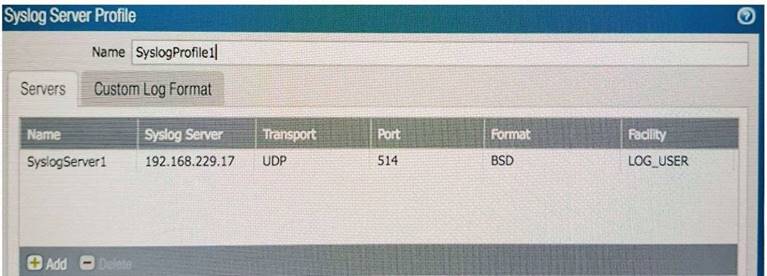
D)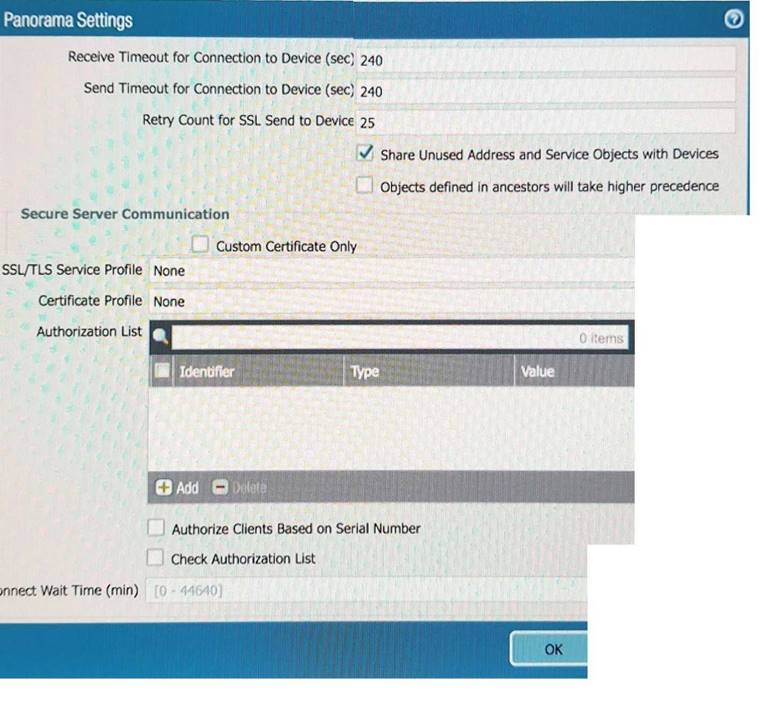
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer: D
NEW QUESTION 27
A network security engineer is asked to provide a report on bandwidth usage. Which tab in the ACC provides the information needed to create the report?
- A. Blocked Activity
- B. Bandwidth Activity
- C. Threat Activity
- D. Network Activity
Answer: D
NEW QUESTION 28
Firewall administrators cannot authenticate to a firewall GUI.
Which two logs on that firewall will contain authentication-related information useful in troubleshooting this issue? (Choose two.)
- A. ms log
- B. authd log
- C. System log
- D. Traffic log
- E. dp-monitor .log
Answer: BC
NEW QUESTION 29
Which Panorama administrator types require the configuration of at least one access domain? (Choose two)
- A. Dynamic
- B. Custom Panorama Admin
- C. Role Based
- D. Device Group E.Template Admin
Answer: DE
NEW QUESTION 30
......
Recommend!! Get the Full PCNSE dumps in VCE and PDF From Certstest, Welcome to Download: https://www.certstest.com/dumps/PCNSE/ (New 255 Q&As Version)