High value of JN0-230 testing engine materials and preparation for Juniper certification for customers, Real Success Guaranteed with Updated JN0-230 pdf dumps vce Materials. 100% PASS Security - Associate (JNCIA-SEC) exam Today!
Free JN0-230 Demo Online For Juniper Certifitcation:
NEW QUESTION 1
Which UTM feature should you use to protect users from visiting certain blacklisted websites?
- A. Content filtering
- B. Web filtering
- C. Antivirus
- D. antispam
Answer: B
NEW QUESTION 2
Exhibit.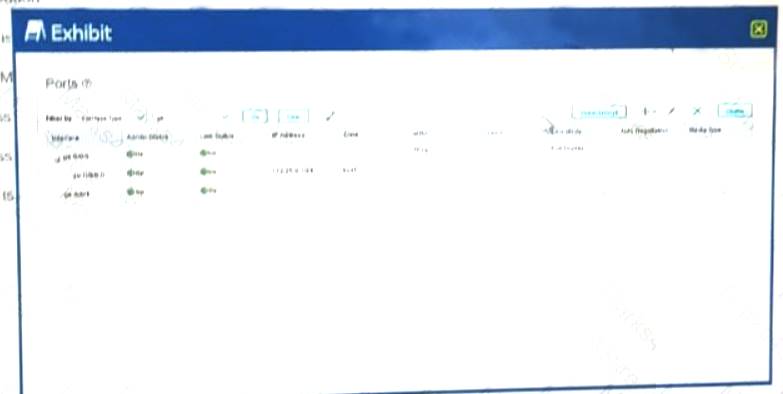
Which statement is correct regarding the interface configuration shown in the exhibit?
- A. The interface MTU has been increased.
- B. The IP address has an invalid subnet mask.
- C. The IP address is assigned to unit 0.
- D. The interface is assigned to the trust zone by default.
Answer: C
NEW QUESTION 3
Which statements is correct about Junos security zones?
- A. User-defined security must contain at least one interface.
- B. Security policies are referenced within a user-defined security zone.
- C. Logical interface are added to user defined security zones
- D. User-defined security must contains the key word ‘’zone’’
Answer: C
NEW QUESTION 4
What are two characteristic of static NAT SRX Series devices? (Choose two.)
- A. Source and destination NAT rules take precedence over static NAT rules.
- B. A reverse mapping rule is automatically created for the source translation.
- C. Static NAT rule take precedence over source and destination NAT rules.
- D. Static rules cannot coexist with destination NAT rules on the same SRX Series device configuration.
Answer: BC
NEW QUESTION 5
The Sky ATP premium or basic-Threat Feed license is needed fort which two features? (Choose two.)
- A. Outbound protection
- B. C&C feeds
- C. Executable inspection
- D. Custom feeds
Answer: BD
NEW QUESTION 6
On an SRX Series device, how should you configure your IKE gateway if the remote endpoint is a branch office-using a dynamic IP address?
- A. Configure the IPsec policy to use MDS authentication.
- B. Configure the IKE policy to use aggressive mode.
- C. Configure the IPsec policy to use aggressive mode.
- D. Configure the IKE policy to use a static IP address
Answer: B
NEW QUESTION 7
Firewall filters define which type of security?
- A. Stateful
- B. Stateless
- C. NGFW
- D. Dynamic enforcement
Answer: B
NEW QUESTION 8
What is the purpose of the Shadow Policies workspace in J-Web?
- A. The Shadow Policies workspace shows unused security policies due to policy overlap.
- B. The Shadow Policies workspace shows unused IPS policies due to policy overlap.
- C. The Shadow Policies workspace shows used security policies due to policy overlap
- D. The Shadow Policies workspace shows used IPS policies due to policy overlap
Answer: A
NEW QUESTION 9
Which statement is correct about IKE?
- A. IKE phase 1 is used to establish the data path
- B. IKE phase 1 only support aggressive mode.
- C. IKE phase 1 negotiates a secure channel between gateways.
- D. IKE phase 1 establishes the tunnel between devices
Answer: C
NEW QUESTION 10
You are configuring an IPsec VPN tunnel between two location on your network. Each packet must be encrypted and authenticated.
Which protocol would satisfy these requirements?
- A. MD5
- B. ESP
- C. AH
- D. SHA
Answer: B
NEW QUESTION 11
You configure and applied several global policies and some of the policies have overlapping match criteria.
- A. In this scenario, how are these global policies applies?
- B. The first matched policy is the only policy applied.
- C. The most restrictive that matches is applied.
- D. The least restrictive policy that matches is applied.
Answer: A
NEW QUESTION 12
Which two statements are true about security policy actions? (Choose two.)
- A. The reject action drops the traffic and sends a message to the source device.
- B. The deny action silently drop the traffic.
- C. The deny action drops the traffic and sends a message to the source device.
- D. The reject action silently drops the traffic.
Answer: AB
NEW QUESTION 13
Which statement about IPsec is correct?
- A. IPsec can be used to transport native Layer 2 packets.
- B. IPsec can provide encapsulation but not encryption
- C. IPsec is a standards-based protocol.
- D. IPsec is used to provide data replication
Answer: C
NEW QUESTION 14
You want to generate reports from the l-Web on an SRX Series device. Which logging mode would you use in this scenario?
- A. Syslog
- B. Stream
- C. Event
- D. local
Answer: B
NEW QUESTION 15
Your company has been assigned one public IP address. You want to enable internet traffic to reach multiple servers in your DMZ that are configured with private address.
In this scenario, which type of NAT would be used to accomplish this tasks?
- A. Static NAT
- B. Destination NAT
- C. Source NAT
- D. NAT without PAT
Answer: B
NEW QUESTION 16
Your company uses SRX Series devices to secure the edge of the network. You are asked protect the company from ransom ware attacks.
Which solution will satisfy this requirement?
- A. Sky ATP
- B. AppSecure
- C. Unified security policies
- D. screens
Answer: A
NEW QUESTION 17
Which statement about IPsec is correct?
- A. IPsec can provide encryption but not data integrity.
- B. IPsec support packet fragmentation by intermediary devices.
- C. IPsec support both tunnel and transport modes.
- D. IPsec must use certificates to provide data encryption
Answer: C
NEW QUESTION 18
Exhibit.
Which two statements are true? (Choose two.)
- A. Logs for this security policy are generated.
- B. Logs for this security policy are not generated.
- C. Traffic static for this security policy are not generated.
- D. Traffic statistics for this security policy are generated.
Answer: AD
NEW QUESTION 19
BY default, revenue interface are placed into which system-defined security zone on an SRX series device?
- A. Trust
- B. Null
- C. Junos-trust
- D. untrust
Answer: D
NEW QUESTION 20
You are designing a new security policy on an SRX Series device. You must block an application and log all occurrence of the application access attempts.
In this scenario, which two actions must be enabled in the security policy? (Choose two.)
- A. Log the session initiations
- B. Enable a reject action
- C. Log the session closures
- D. Enable a deny action
Answer: AD
NEW QUESTION 21
......
Recommend!! Get the Full JN0-230 dumps in VCE and PDF From Passcertsure, Welcome to Download: https://www.passcertsure.com/JN0-230-test/ (New 65 Q&As Version)