Cause all that matters here is passing the Juniper JN0-664 exam. Cause all that you need is a high score of JN0-664 Service Provider - Professional (JNCIP-SP) exam. The only one thing you need to do is downloading Certleader JN0-664 exam study guides now. We will not let you down with our money-back guarantee.
Free demo questions for Juniper JN0-664 Exam Dumps Below:
NEW QUESTION 1
You are responding to an RFP for a new MPLS VPN implementation. The solution must use LDP for signaling and support Layer 2 connectivity without using BGP The solution must be scalable and support multiple VPN connections over a single MPLS LSP The customer wants to maintain all routing for their Private network
In this scenario, which solution do you propose?
- A. circuit cross-connect
- B. BGP Layer 2 VPN
- C. LDP Layer 2 circuit
- D. translational cross-connect
Answer: C
Explanation:
AToM (Any Transport over MPLS) is a framework that supports various Layer 2 transport types over an MPLS network core. One of the transport types supported by AToM is LDP Layer 2 circuit, which is a point-to-point Layer 2 connection that uses LDP for signaling and MPLS for forwarding. LDP Layer 2 circuit can support Layer 2 connectivity without using BGP and can be scalable and efficient by using a single MPLS LSP for multiple VPN connections. The customer can maintain all routing for their private network by using their own CE switches.
NEW QUESTION 2
Exhibit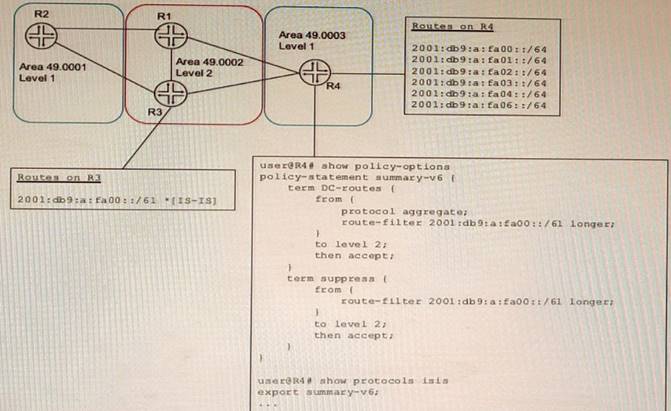
A network designer would like to create a summary route as shown in the exhibit, but the
configuration is not working.
Which three configuration changes will create a summary route? (Choose three.)
- A. set policy-options policy-statement leak-v6 term DC-routes then reject
- B. delete policy-options policy-statement leak-v6 term DC-routes from route-filter 2001: db9:a: fa00 : :/6l longer
- C. set policy—options policy-statement leak-v€ term DC—routes from route-filter 2001:db9:a:faOO::/61 exact
- D. delete protocols isis export summary-v6
- E. set protocols isis import summary-v6
Answer: BCD
Explanation:
To create a summary route for IS-IS, you need to configure a policy statement that matches the prefixes to be summarized and sets the next-hop to discard. You also need to configure a summary-address statement under the IS-IS protocol hierarchy that references the policy statement. In this case, the policy statement leak-v6 is trying to match the prefix 2001:db9:a:fa00::/61 exactly, but this prefix is not advertised by any router in the network. Therefore, no summary route is created. To fix this, you need to delete the longer keyword from the route-filter term and change the prefix length to /61 exact. This will match any prefix that falls within the /61 range. You also need to delete the export statement under protocols isis, because this will export all routes that match the policy statement to other IS-IS routers, which is not desired for a summary route.
NEW QUESTION 3
Which three mechanisms are used by Junos platforms to evaluate incoming traffic for CoS purposes? (Choose three )
- A. rewrite rules
- B. behavior aggregate classifiers
- C. traffic shapers
- D. fixed classifiers
- E. multifield classifiers
Answer: BDE
Explanation:
Junos platforms use different mechanisms to evaluate incoming traffic for CoS purposes, such as:
✑ Behavior aggregate classifiers: These classifiers use a single field in a packet header to classify traffic into different forwarding classes and loss priorities based on predefined or user-defined values.
✑ Fixed classifiers: These classifiers use a fixed field in a packet header to classify traffic into different forwarding classes and loss priorities based on predefined values.
✑ Multifield classifiers: These classifiers use multiple fields in a packet header to classify traffic into different forwarding classes and loss priorities based on user- defined values and filters.
Rewrite rules and traffic shapers are not used to evaluate incoming traffic for CoS purposes, but rather to modify or shape outgoing traffic based on CoS policies.
NEW QUESTION 4
You are configuring a BGP signaled Layer 2 VPN across your MPLS enabled core network. Your PE-2 device connects to two sites within the s VPN
In this scenario, which statement is correct?
- A. By default on PE-2, the site's local ID is automatically assigned a value of 0 and must be configured to match the total number of attached sites.
- B. You must create a unique Layer 2 VPN routing instance for each site on the PE-2 device.
- C. You must use separate physical interfaces to connect PE-2 to each site.
- D. By default on PE-2, the remote site IDs are automatically assigned based on the order that you add the interfaces to the site configuration.
Answer: D
Explanation:
BGP Layer 2 VPNs use BGP to distribute endpoint provisioning information and set up pseudowires between PE devices. BGP uses the Layer 2 VPN (L2VPN) Routing Information Base (RIB) to store endpoint provisioning information, which is updated each time any Layer 2 virtual forwarding instance (VFI) is configured. The prefix and path information is stored in the L2VPN database, which allows BGP to make decisions about the best path.
In BGP Layer 2 VPNs, each site has a unique site ID that identifies it within a VFI. The site ID can be manually configured or automatically assigned by the PE device. By default, the site ID is automatically assigned based on the order that you add the interfaces to the site configuration. The first interface added to a site configuration has a site ID of 1, the second interface added has a site ID of 2, and so on.
Option D is correct because by default on PE-2, the remote site IDs are automatically assigned based on the order that you add the interfaces to the site configuration. Option A is not correct because by default on PE-2, the site’s local ID is automatically assigned a value of 0 and does not need to be configured to match the total number of attached sites. Option B is not correct because you do not need to create a unique Layer 2 VPN routing instance for each site on the PE-2 device. You can create one routing instance for all sites within a VFI. Option C is not correct because you do not need to use separate physical interfaces to connect PE-2 to each site. You can use subinterfaces or service instances on a single physical interface.
NEW QUESTION 5
An interface is configured with a behavior aggregate classifier and a multifield classifier How will the packet be processed when received on this interface?
- A. The packet will be discarded.
- B. The packet will be processed by the BA classifier first, then the MF classifier.
- C. The packet will be forwarded with no classification changes.
- D. The packet will be processed by the MF classifier first, then the BA classifier.
Answer: C
Explanation:
behavior aggregate (BA) classifiers and multifield (MF) classifiers are two types of classifiers that are used to assign packets to a forwarding class and a loss priority based on different criteria. The forwarding class determines the output queue for a packet. The loss priority is used by a scheduler to control packet discard during periods of congestion.
A BA classifier maps packets to a forwarding class and a loss priority based on a fixed- length field in the packet header, such as DSCP, IP precedence, MPLS EXP, or IEEE 802.1p CoS bits. A BA classifier is computationally efficient and suitable for core devices that handle high traffic volumes. A BA classifier is useful if the traffic comes from a trusted source and the CoS value in the packet header is trusted.
An MF classifier maps packets to a forwarding class and a loss priority based on multiple fields in the packet header, such as source address, destination address, protocol type, port number, or VLAN ID. An MF classifier is more flexible and granular than a BA classifier and can match packets based on complex filter rules. An MF classifier is suitable for edge devices that need to classify traffic from untrusted sources or rewrite packet headers.
You can configure both a BA classifier and an MF classifier on an interface. If you do this, the BA classification is performed first and then the MF classification. If the two classification results conflict, the MF classification result overrides the BA classification result.
Based on this information, we can infer the following statements:
✑ The packet will be discarded. This is not correct because the packet will not be discarded by the classifiers unless it matches a filter rule that specifies discard as an action. The classifiers only assign packets to a forwarding class and a loss priority based on their match criteria.
✑ The packet will be processed by the BA classifier first, then the MF classifier. This is correct because if both a BA classifier and an MF classifier are configured on an interface, the BA classification is performed first and then the MF classification. If they conflict, the MF classification result overrides the BA classification result.
✑ The packet will be forwarded with no classification changes. This is not correct because the packet will be classified by both the BA classifier and the MF classifier if they are configured on an interface. The final classification result will determine which output queue and which discard policy will be applied to the packet.
✑ The packet will be processed by the MF classifier first, then the BA classifier. This is not correct because if both a BA classifier and an MF classifier are configured on an interface, the BA classification is performed first and then the MF classification. If they conflict, the MF classification result overrides the BA classification result.
NEW QUESTION 6
Exhibit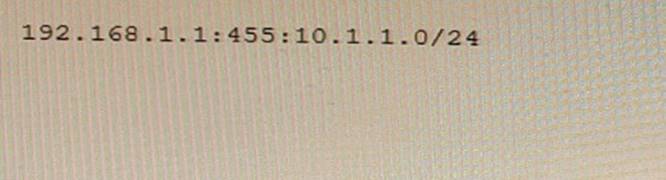
You are examining an L3VPN route that includes the information shown in the exhibit Which statement is correct in this scenario?
- A. The information shows a Type 1 route distinguisher.
- B. The information shows a Type 0 route distinguisher
- C. The information shows a Type 2 route distinguisher.
- D. The information shows a route target
Answer: B
Explanation:
The information shows a Type 0 route distinguisher, which is one of the three types of route distinguishers defined by RFC 4364. A route distinguisher is a 64-bit value that is prepended to an IPv4 address to create a VPN-IPv4 address, which is unique within a VPN routing and forwarding (VRF) table. A Type 0 route distinguisher has two fields: an administrator subfield (2 bytes) and an assigned number subfield (6 bytes). The administrator subfield can be an AS number or an IP address, and the assigned number subfield can be any value assigned by the administrator. In this example, the administrator subfield is 65530 (an AS number) and the assigned number subfield is 1.
NEW QUESTION 7
Exhibit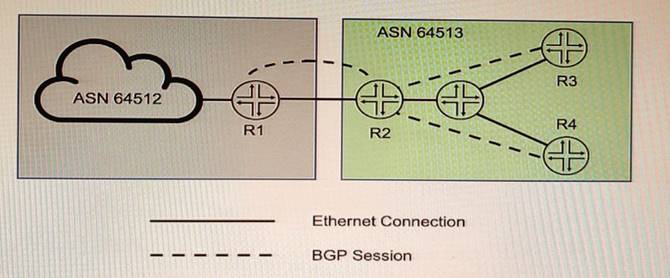
You want to implement the BGP Generalized TTL Security Mechanism (GTSM) on the network
Which three statements are correct in this scenario? (Choose three)
- A. You can implement BGP GTSM between R2, R3, and R4
- B. BGP GTSM requires a firewall filter to discard packets with incorrect TTL.
- C. You can implement BGP GTSM between R2 and R1.
- D. BGP GTSM requires a TTL of 1 to be configured between neighbors.
- E. BGP GTSM requires a TTL of 255 to be configured between neighbors.
Answer: ADE
Explanation:
BGP GTSM is a technique that protects a BGP session by comparing the TTL value in the IP header of incoming BGP packets against a valid TTL range. If the TTL value is within the valid TTL range, the packet is accepted. If not, the packet is discarded. The valid TTL range is from 255 – the configured hop count + 1 to 255. When GTSM is configured, the BGP packets sent by the device have a TTL of 255. GTSM provides best protection for directly connected EBGP sessions, but not for multihop EBGP or IBGP sessions because the TTL of packets might be modified by intermediate devices.
In the exhibit, we can see that R2, R3, and R4 are in the same AS (AS 20) and R1 is in a different AS (AS 10). Based on this information, we can infer the following statements:
✑ You can implement BGP GTSM between R2, R3, and R4. This is not correct because R2, R3, and R4 are IBGP peers and GTSM does not provide effective protection for IBGP sessions. The TTL of packets between IBGP peers might be changed by intermediate devices or routing protocols.
✑ BGP GTSM requires a firewall filter to discard packets with incorrect TTL. This is not correct because BGP GTSM does not require a firewall filter to discard packets with incorrect TTL. BGP GTSM uses TCP option 19 to negotiate GTSM capability between peers and uses TCP option 20 to carry the expected TTL value in each packet. The receiver checks the expected TTL value against the actual TTL value and discards packets with incorrect TTL values.
✑ You can implement BGP GTSM between R2 and R1. This is correct because R2 and R1 are EBGP peers and GTSM provides effective protection for directly connected EBGP sessions. The TTL of packets between directly connected EBGP peers is not changed by intermediate devices or routing protocols.
✑ BGP GTSM requires a TTL of 1 to be configured between neighbors. This is not correct because BGP GTSM requires a TTL of 255 to be configured between neighbors. The sender sets the TTL of packets to 255 and the receiver expects the TTL of packets to be 255 minus the configured hop count.
✑ BGP GTSM requires a TTL of 255 to be configured between neighbors. This is correct because BGP GTSM requires a TTL of 255 to be configured between neighbors. The sender sets the TTL of packets to 255 and the receiver expects the TTL of packets to be 255 minus the configured hop count.
NEW QUESTION 8
You are a network architect for a service provider and want to offer Layer 2 services to your customers You want to use EVPN for Layer 2 services in your existing MPLS network.
Which two statements are correct in this scenario? (Choose two.)
- A. Segment routing must be configured on all PE routers.
- B. VXLAN must be configured on all PE routers.
- C. EVPN uses Type 2 routes to advertise MAC address and IP address pairs learned using ARP snooping
- D. EVPN uses Type 3 routes to join a multicast tree to flood traffic.
Answer: CD
Explanation:
EVPN is a technology that connects L2 network segments separated by an L3 network using a virtual Layer 2 network overlay over the Layer 3 network. EVPN uses BGP as its control protocol to exchange different types of routes for different purposes. Type 2 routes are used to advertise MAC address and IP address pairs learned using ARP snooping from the local CE devices. Type 3 routes are used to join a multicast tree to flood traffic such as broadcast, unknown unicast, and multicast (BUM) traffic.
NEW QUESTION 9
Exhibit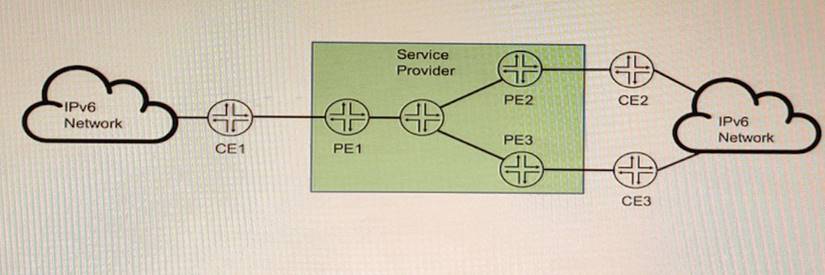
You are running a service provider network and must transport a customer's IPv6 traffic across your IPv4-based MPLS network using BGP You have already configured mpis ipv6- tunneling on your PE routers.
Which two statements are correct about the BGP configuration in this scenario? (Choose two.)
- A. You must configure family inet6 labcled-unicast between PE routers.
- B. You must configure family inet6 unicaat between PE and CE routers.
- C. You must configure family inet6 add-path between PE and CE routers.
- D. You must configure family inet6 unicast between PE routers
Answer: AB
Explanation:
To transport IPv6 traffic over an IPv4-based MPLS network using BGP, you need to configure two address families: family inet6 labeled-unicast and family inet6 unicast. The former is used to exchange IPv6 routes with MPLS labels between PE routers, and the latter is used to exchange IPv6 routes without labels between PE and CE routers. The mpis ipv6-tunneling command enables the PE routers to encapsulate the IPv6 packets with an MPLS label stack and an IPv4 header before sending them over the MPLS network.
NEW QUESTION 10
Exhibit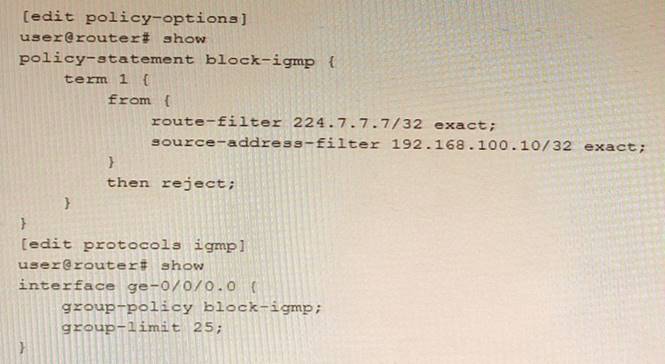
Based on the configuration contents shown in the exhibit, which statement is true?
- A. Joins for group 224.7.7.7 are rejected if the source address is 192.168.100.10
- B. Joins for any group are accepted if the group count value is less than 25.
- C. Joins for group 224.7.7.7 are always rejected, regardless of the group count.
- D. Joins for group 224.7.7.7 are accepted if the group count is less than 25
Answer: D
Explanation:
BGP policy framework is a set of tools that allows you to control the flow of routing information and apply routing policies based on various criteria. BGP policy framework consists of several components, such as route maps, prefix lists, community lists, AS path lists, and route filters. Route maps are used to define routing policies by matching certain conditions and applying certain actions. Prefix lists are used to filter routes based on their prefixes. Community lists are used to filter routes based on their community attributes. AS path lists are used to filter routes based on their AS path attributes. Route filters are used to filter routes based on their prefix length or range3. In this question, we have a route map named ISP-A that has two clauses: clause 10 and clause 20. Clause 10 matches any route with a prefix length between 8 and 24 bits and sets the local preference to 200. Clause 20 matches any route with a prefix of 224.7.7.7/32 and rejects it. The route map is applied inbound on the BGP neighborship with ISP-A. Based on this configuration, the correct statement is that joins for group 224.7.7.7 are always rejected, regardless of the group count. This is because clause 20 explicitly denies any route with a prefix of 224.7.7.7/32, which corresponds to the multicast group 224.7.7.7.
Reference: 3: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_bgp/configuration/xe-16/irg-xe-16-book/bgp-policy-framework.html
NEW QUESTION 11
Exhibit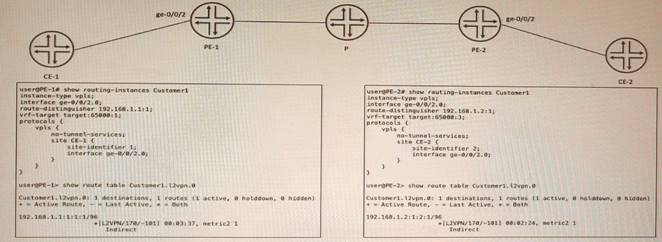
CE-1 and CE-2 are part of a VPLS called Customer1 No connectivity exists between CE-1 and CE-2. In the process of troubleshooting, you notice PE-1 is not learning any routes for this VPLS from PE-2, and PE-2 is not learning any routes for this VPLS from PE-1.
- A. The route target must match on PE-1 and PE-2.
- B. The route distinguisher must match on PE-1 and PE-2.
- C. The instance type should be changed to I2vpn.
- D. The no-tunnel-services statement should be deleted on both PEs.
Answer: A
Explanation:
VPLS is a technology that provides Layer 2 VPN services over an MPLS network. VPLS uses BGP as its control protocol to exchange VPN membership information between PE routers. The route target is a BGP extended community attribute that identifies which VPN a route belongs to. The route target must match on PE routers that participate in the same VPLS instance, otherwise they will not accept or advertise routes for that VPLS.
NEW QUESTION 12
Exhibit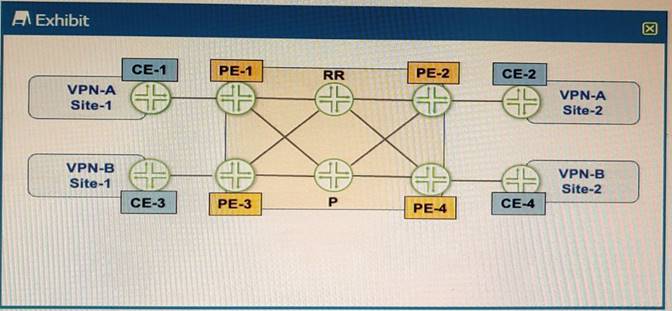
Referring to the exhibit, PE-1 and PE-2 are getting route updates for VPN-B when neither of them service that VPN
Which two actions would optimize this process? (Choose two.)
- A. Configure the family route-target statement on the PEs.
- B. Configure the family route-target statement on the RR
- C. Configure the resolution rib bgp . 13vpn . 0 resolution-ribs ine
- D. 0 Statement on the PEs.
- E. Configure the resolution rib bgp.l3vpn.O resolution-ribs ine
- F. 0 Statement on the RR
Answer: BD
Explanation:
BGP route target filtering is a technique that reduces the number of routers that receive VPN routes and route updates, helping to limit the amount of overhead associated with running a VPN. BGP route target filtering is based on the exchange of the route-target address family, which contains information about the VPN membership of each PE device. Based on this information, a PE device can decide whether to accept or reject VPN routes from another PE device.
BGP route target filtering can be configured on PE devices or on route reflectors (RRs). Configuring BGP route target filtering on RRs is more efficient and scalable, as it reduces the number of BGP sessions and updates between PE devices. To configure BGP route target filtering on RRs, the following steps are required:
✑ Configure the family route-target statement under the BGP group or neighbor configuration on the RRs. This enables the exchange of the route-target address family between the RRs and their clients (PE devices).
✑ Configure the resolution rib bgp.l3vpn.0 resolution-ribs inet.0 statement under the routing-options configuration on the RRs. This enables the RRs to resolve next hops for VPN routes using the inet.0 routing table.
✑ Configure an export policy for BGP route target filtering under the routing-options configuration on the RRs. This policy controls which route targets are advertised to each PE device based on their VPN membership.
NEW QUESTION 13
In IS-IS, which two statements are correct about the designated intermediate system (DIS) on a multi-access network segment? (Choose two)
- A. A router with a priority of 10 wins the DIS election over a router with a priority of 1.
- B. A router with a priority of 1 wins the DIS election over a router with a priority of 10.
- C. On the multi-access network, each router forms an adjacency to every other router on the segment
- D. On the multi-access network, each router only forms an adjacency to the DIS.
Answer: AD
Explanation:
In IS-IS, a designated intermediate system (DIS) is a router that is elected on a multi-access network segment (such as Ethernet) to perform some functions on behalf of other routers on the same segment. A DIS is responsible for sending network link-state advertisements (LSPs), which describe all the routers attached to the network. These LSPs are flooded throughout a single area. A DIS also generates pseudonode LSPs, which represent the multi-access network as a single node in the link-state database. A DIS election is based on the priority value configured on each router’s interface connected to the multi-access network. The priority value ranges from 0 to 127, with higher values indicating higher priority. The router with the highest priority becomes the DIS for the area (Level 1, Level 2, or both). If routers have the same priority, then the router with the highest MAC address is elected as the DIS. By default, routers have a priority value of 64. On a multi-access network, each router only forms an adjacency to the DIS, not to every other router on the segment. This reduces the amount of hello packets and LSP
NEW QUESTION 14
Exhibit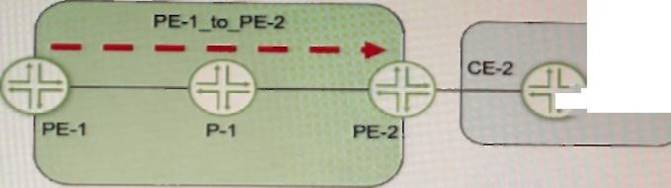
Referring to the exhibit, a working L3VPN exists that connects VPN-A sites CoS is configured correctly to match on the MPLS EXP bits of the LSP, but when traffic is sent from Site-1 to Site-2, PE-2 is not classifying the traffic correctly
What should you do to solve the problem?
- A. Configure the explicit-null statement on PE-1.
- B. Configure the explicit-null statement on PE-2
- C. Configure VPN prefix mapping for the PE-1_to_PE-2 LSP
- D. Set a static CoS value for the PE-1_to_PE-2 LSP
Answer: A
Explanation:
The explicit-null statement enables the PE router to send an MPLS label with a value of 0 (explicit null) instead of an IP header for packets destined to the VPN customer sites. This allows the penultimate hop router (the router before the egress PE router) to preserve the EXP bits of the MPLS label and pass them to the egress PE router. The egress PE router can then use these EXP bits to classify the traffic according to the CoS policy2. In this example, PE-1 should configure the explicit-null statement under [edit protocols mpls label-switched-path PE-1_to_PE-2] hierarchy level.
NEW QUESTION 15
A packet is received on an interface configured with transmission scheduling. One of the configured queues In this scenario, which two actions will be taken by default on a Junos device? (Choose two.)
- A. The excess traffic will be discarded
- B. The exceeding queue will be considered to have negative bandwidth credit.
- C. The excess traffic will use bandwidth available from other queueses
- D. The exceeding queue will be considered to have positive bandwidth credit
Answer: AB
Explanation:
Transmission scheduling is a CoS feature that allows you to allocate bandwidth among different queues on an interface. Each queue has a configured bandwidth percentage that determines how much of the available bandwidth it can use. If a queue exceeds its allocated bandwidth, it is considered to have negative bandwidth credit and its excess traffic will be discarded by default. If a queue does not use all of its allocated bandwidth, it is considered to have positive bandwidth credit and its unused bandwidth can be shared by other queues.
NEW QUESTION 16
Your organization manages a Layer 3 VPN for multiple customers To support advanced route than one BGP community on advertised VPN routes to remote PE routers.
Which routing-instance configuration parameter would support this requirement?
- A. vrf-export
- B. vrf-import
- C. vrf-target export
- D. vrf-target import
Answer: C
Explanation:
The vrf-target export parameter is used to specify one or more BGP extended community attributes that are attached to VPN routes when they are exported from a VRF routing instance to remote PE routers. This parameter allows you to control which VPN routes are accepted by remote PE routers based on their import policies. You can specify more than one vrf-target export value for a VRF routing instance to support advanced route filtering or route leaking scenarios.
NEW QUESTION 17
Exhibit
You must ensure that the VPN backbone is preferred over the back door intra-area link as long as the VPN is available. Referring to the exhibit, which action will accomplish this task?
- A. Configure an import routing policy on the CE routers that rejects OSPF routes learned on the backup intra-area link.
- B. Enable OSPF traffic-engineering.
- C. Configure the OSPF metric on the backup intra-area link that is higher than the L3VPN link.
- D. Create an OSPF sham link between the PE routers.
Answer: D
Explanation:
A sham link is a logical link between two PE routers that belong to the same OSPF area but are connected through an L3VPN. A sham link makes the PE routers appear as if they are directly connected, and prevents OSPF from preferring an intra-area back door link over the VPN backbone. To create a sham link, you need to configure the local and remote addresses of the PE routers under the [edit protocols ospf area area-id] hierarchy level1.
NEW QUESTION 18
Exhibit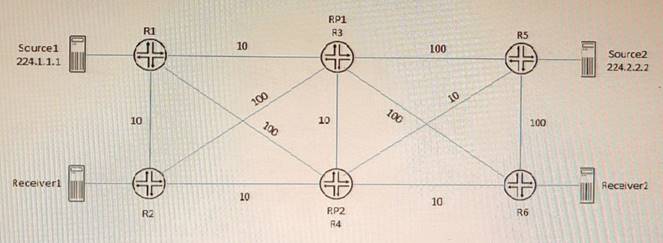
Referring to the exhibit, PIM-SM is configured on all routers, and Anycast-RP with Anycast- PIM is used for the discovery mechanism on RP1 and RP2. The interface metric values are shown for the OSPF area.
In this scenario, which two statements are correct about which RP is used? (Choose two.)
- A. Source2 will use RP2 and Received will use RP2 for group 224.2.2.2.
- B. Source2 will use RP1 and Receiver2 will use RP1 for group 224.2.2.2.
- C. Source1 will use RP1 and Receiver1 will use RP1 for group 224.1.1.1.
- D. Source1 will use RP1 and Receiver1 will use RP2 for group 224.1 1 1
Answer: AC
Explanation:
A sham link is a logical link between two PE routers that belong to the same OSPF area but are connected through an L3VPN. A sham link makes the PE routers appear as if they are directly connected, and prevents OSPF from preferring an intra-area back door link over the VPN backbone. A sham link creates an OSPF multihop neighborship between the PE routers using TCP port 646. The PEs exchange Type 1 OSPF LSAs instead of Type 3 OSPF LSAs for the L3VPN routes, which allows OSPF to use the correct metric for route selection1.
NEW QUESTION 19
......
Thanks for reading the newest JN0-664 exam dumps! We recommend you to try the PREMIUM Certleader JN0-664 dumps in VCE and PDF here: https://www.certleader.com/JN0-664-dumps.html (65 Q&As Dumps)