Pass4sure N10-008 Questions are updated and all N10-008 answers are verified by experts. Once you have completely prepared with our N10-008 exam prep kits you will be ready for the real N10-008 exam without a problem. We have Far out CompTIA N10-008 dumps study guide. PASSED N10-008 First attempt! Here What I Did.
Free demo questions for CompTIA N10-008 Exam Dumps Below:
NEW QUESTION 1
Which of the following is used to elect an STP root?
- A. A bridge ID
- B. A bridge protocol data unit
- C. Interface port priority
- D. A switch's root port
Answer: B
Explanation:
"Using special STP frames known as bridge protocol data units (BPDUs), switches communicate with other switches to prevent loops from happening in the first place. Configuration BPDUs establish the topology, where one switch is elected root bridge and acts as the center of the STP universe. Each switch then uses the root bridge as a reference point to maintain a loop-free topology."
NEW QUESTION 2
A large number of PCs are obtaining an APIPA IP address, and a number of new computers were added to the network. Which of the following is MOST likely causing the PCs to obtain an APIPA address?
- A. Rogue DHCP server
- B. Network collision
- C. Incorrect DNS settings
- D. DHCP scope exhaustion
Answer: D
Explanation:
DHCP scope exhaustion means that there are no more available IP addresses in the DHCP server’s pool of addresses to assign to new devices on the network. When this happens, the devices will use APIPA (Automatic Private IP Addressing) to self-configure an IP address in the range of 169.254.0.1 to 169.254.255.2541. These addresses are not routable and can only communicate with other devices on the same local network.
A rogue DHCP server (A) is an unauthorized DHCP server that can cause IP address conflicts or security issues by assigning IP addresses to devices on the network. A network collision (B) is a situation where two or more devices try to send data on the same network segment at the same time, causing interference and data loss. Incorrect DNS settings © can prevent devices from resolving domain names to IP addresses, but they do not affect the DHCP process.
NEW QUESTION 3
A network engineer is configuring new switches. Some of the trunk ports are in a blocking state. Which of the following should the network engineer
reconfigure?
- A. STP
- B. Port mirroring
- C. Flow control
- D. LACP
Answer: A
Explanation:
STP (Spanning Tree Protocol) is a protocol that prevents loops in a network by placing some of the switch ports in different states, such as blocking, listening, learning, forwarding, or disabled. A port in the blocking state does not forward frames or participate in frame forwarding. A network engineer can reconfigure STP to change the port states and avoid blocking ports that are needed for trunking.
NEW QUESTION 4
A network technician wants to find the shortest path from one node to every other node in the network. Which of the following algorithms will provide the FASTEST convergence time?
- A. A static algorithm
- B. A link-state algorithm
- C. A distance-vector algorithm
- D. A path-vector algorithm
Answer: B
Explanation:
A link-state algorithm is a routing algorithm that uses information about the state of each link in the network to calculate the shortest path from one node to every other node. A link-state algorithm requires each router to maintain a complete map of the network topology and exchange link-state advertisements with its neighbors periodically or when a change occurs. A link-state algorithm uses a mathematical formula called Dijkstra’s algorithm to find the shortest path based on the link costs. A link-state algorithm provides the fastest convergence time because it can quickly detect and adapt to network changes. References: [CompTIA Network+ Certification Exam Objectives], [Link-state routing protocol - Wikipedia]
NEW QUESTION 5
A network administrator views a network pcap and sees a packet containing the following: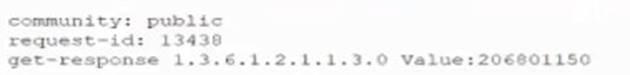
Which of the following are the BEST ways for the administrator to secure this type of traffic? (Select TWO).
- A. Migrate the network to IPv6.
- B. Implement 802.1 X authentication
- C. Set a private community siring
- D. Use SNMPv3.
- E. Incorporate SSL encryption
- F. Utilize IPSec tunneling.
Answer: CD
Explanation:
The packet shown in the image is an SNMP (Simple Network Management Protocol) packet, which is used to monitor and manage network devices. SNMP uses community strings to authenticate requests and responses between SNMP agents and managers. However, community strings are sent in clear text and can be easily intercepted by attackers. Therefore, one way to secure SNMP traffic is to set a private community string that is not the default or well-known value. Another way to secure SNMP traffic is to use SNMPv3, which is the latest version of the protocol that supports encryption and authentication of SNMP messages.
References: CompTIA Network+ Certification Exam Objectives Version 7.0 (N10-007), Objective 2.5: Given a scenario, use remote access methods.
NEW QUESTION 6
An organization wants to implement a method of centrally managing logins to network services. Which of the following protocols should the organization use to allow for authentication, authorization and auditing?
- A. MS-CHAP
- B. RADIUS
- C. LDAPS
- D. RSTP
Answer: B
Explanation:
RADIUS (Remote Authentication Dial-In User Service) is a protocol that should be used by the organization to allow for authentication, authorization, and auditing of network services. RADIUS is an AAA (Authentication, Authorization, and Accounting) protocol that manages network access by verifying user credentials, granting access permissions, and logging user activities. RADIUS uses a client-server model where a RADIUS client (such as a router, switch, or VPN server) sends user information to a RADIUS server (such as an authentication server) for verification and authorization. The RADIUS server can also send accounting information to another server for billing or reporting purposes. References: https://www.cisco.com/c/en/us/support/docs/security- vpn/remote-authentication-dial-user-service-radius/13838-10.html
NEW QUESTION 7
Which of the following protocol types describes secure communication on port 443?
- A. ICMP
- B. UDP
- C. TCP
- D. IP
Answer: C
Explanation:
TCP is the protocol type that describes secure communication on port 443. TCP (Transmission Control Protocol) is a connection-oriented protocol that provides reliable and ordered delivery of data packets over an IP network. TCP uses port numbers to identify different applications or services on a device. Port 443 is the default port for HTTPS (Hypertext Transfer Protocol Secure), which is an extension of HTTP that uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) encryption to protect data in transit between a web server and a web browser. References: https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13788- 3.html
NEW QUESTION 8
A small office has a wireless network with several access points that are used by mobile devices. Users occasionally report that the wireless connection drops or becomes very slow. Reports confirm that this only happens when the devices are connected to the office wireless network. Which of the following is MOST likely the cause?
- A. The configuration of the encryption protocol
- B. Interference from other devices
- C. Insufficient bandwidth capacity
- D. Duplicate SSIDs
Answer: B
Explanation:
Interference from other devices can cause wireless connection drops or slow performance. This can happen when devices use the same or overlapping frequency channels as the wireless network, such as cordless phones, microwaves, Bluetooth devices, etc. To avoid interference, it is recommended to use non-overlapping channels and avoid placing wireless access points near potential sources of interference. References: Network+ Study Guide Objective 2.1: Explain the purposes and use cases for advanced network devices. Subobjective: Wireless controllers.
NEW QUESTION 9
A network is experiencing extreme latency when accessing a particular website. Which of the following commands will BEST help identify the issue?
- A. ipconfig
- B. netstat
- C. tracert
- D. ping
Answer: C
NEW QUESTION 10
Two companies want to build an encrypted tunnel between them and use a PSK for initial authentication. Which of the following is the BEST protocol for the companies to use?
- A. VPN
- B. SSL
- C. TLS
- D. IPSec
Answer: D
Explanation:
IPSec is a protocol that provides secure communication between two networks or hosts over an untrusted network, such as the Internet. IPSec uses encryption and authentication to protect the data from eavesdropping, tampering, and replay attacks. IPSec also supports pre-shared key (PSK) as one of the methods for initial authentication between the peers
NEW QUESTION 11
A network technician is selecting new network hardware, and availability is the main concern. Which of the following availability concepts should the technician consider?
- A. RTO
- B. MTTR
- C. MTBF
- D. RPO
Answer: A
Explanation:
The availability concept that the network technician should consider when selecting new network hardware is RTO (Recovery Time Objective). RTO is a metric that defines the maximum acceptable time for restoring a system or service after a disruption or failure. RTO is based on the impact and cost of downtime for the business and its customers. RTO helps determine the level of redundancy and backup needed for network hardware to ensure high availability and minimize downtime. References: CompTIA Network+ N10-008 Certification Study Guide, page 346; The Official CompTIA Network+ Student Guide (Exam N10-008), page 13-9.
NEW QUESTION 12
A network administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
- A. A physical interface used for trunking logical ports
- B. A physical interface used for management access
- C. A logical interface used for the routing of VLANs
- D. A logical interface used when the number of physical ports is insufficient
Answer: C
Explanation:
An SVI, or switched virtual interface, is a logical interface that is created on a Layer 3- capable device, such as a multilayer switch or a router. An SVI is associated with a VLAN and can be used to route traffic between different VLANs on the same device or across multiple devices. An SVI can also provide management access, security features, and quality of service (QoS) for the VLAN. An SVI is different from a physical interface, which is a port that connects to a physical device or network. A physical interface can be used for trunking, which is a method of carrying multiple VLANs over a single link, or for connecting to a single VLAN. An SVI is also different from a subinterface, which is a logical division of a physical interface that can be assigned to different VLANs.
References:
✑ VLANs and Trunking – N10-008 CompTIA Network+ : 2.11
✑ Switched Virtual Interfaces – N10-008 CompTIA Network+ : 2.22
NEW QUESTION 13
Which of the following should a network administrator configure when adding OT devices to an organization's architecture?
- A. Honeynet
- B. Data-at-rest encryption
- C. Time-based authentication
- D. Network segmentation
Answer: D
Explanation:
Network segmentation is the process of dividing a network into smaller subnets or segments, each with its own security policies and access controls. This can help isolate OT devices from IT devices, guest networks, and other potential threats, as well as improve network performance and efficiency. Network segmentation is a recommended security practice for OT environments, as it can limit the attack surface, contain the damage of a breach, and comply with regulatory standards.
https://sectrio.com/complete-guide-to-ot-network-segmentation/
NEW QUESTION 14
A network security technician is designing a solution for a secure remote access scheme with the following requirements:
• The solution must allow for users at multiple locations to access corporate resources.
• The on-premises equipment will not handle non-corporate, resource-bound traffic.
Which of the following should the network security technician consider when designing the solution? (Select two).
- A. Clientless VPN
- B. Personal VPN
- C. Full-tunnel VPN
- D. Client-to-site VPN
- E. Site-to-site VPN
- F. Split-tunnel VPN
Answer: DF
Explanation:
A client-to-site VPN and a split-tunnel VPN are the best options for designing a secure remote access scheme that meets the given requirements. A client-to-site VPN allows users at multiple locations to access corporate resources over the internet by creating a secure tunnel between their devices and a VPN concentrator on the corporate network1. A split-tunnel VPN allows the on-premises equipment to handle only the traffic that is destined for the corporate resources, while the non-corporate traffic is routed directly to the internet without passing through the VPN tunnel2. This reduces the bandwidth and processing load on the corporate network and improves the performance of the remote access.
References:
✑ Remote Access – N10-008 CompTIA Network+ : 4.41
✑ comptia Network+ : Remote Access Methods And Network Monitoring2
NEW QUESTION 15
To reduce costs and increase mobility, a Chief Technology Officer (CTO) wants to adopt cloud services for the organization and its affiliates. To reduce the impact for users, the CTO wants key services to run from the on-site data center and enterprise services to run in the cloud. Which of the following deployment models is the best choice for the organization?
- A. Public
- B. Hybrid
- C. SaaS
- D. Private
Answer: B
Explanation:
A hybrid cloud deployment model is a combination of on-premise and cloud solutions, where some resources are hosted in-house and some are hosted by a cloud provider. A hybrid cloud model can offer the benefits of both public and private clouds, such as scalability, cost-efficiency, security, and control12. A hybrid cloud model can also reduce the impact for users, as they can access the key services from the on-site data center and the enterprise services from the cloud
NEW QUESTION 16
A lab environment hosts Internet-facing web servers and other experimental machines, which technicians use for various tasks A technician installs software on one of the web servers to allow communication to the company's file server, but it is unable to connect to it Other machines in the building are able to retrieve files from the file server. Which of the following is the MOST likely reason the web server cannot retrieve the files, and what should be done to resolve the problem?
- A. The lab environment's IDS is blocking the network traffic 1 he technician can whitelist the new application in the IDS
- B. The lab environment is located in the DM2, and traffic to the LAN zone is denied by defaul
- C. The technician can move the computer to another zone or request an exception from the administrator.
- D. The lab environment has lost connectivity to the company router, and the switch needs to be reboote
- E. The technician can get the key to the wiring closet and manually restart the switch
- F. The lab environment is currently set up with hubs instead of switches, and the requests are getting bounced back The technician can submit a request for upgraded equipment to management.
Answer: B
Explanation:
The lab environment is located in the DMZ, and traffic to the LAN zone is denied by default. This is the most likely reason why the web server cannot retrieve files from the file server, and the technician can either move the computer to another zone or request an exception from the administrator to resolve the problem. A DMZ (Demilitarized Zone) is a network segment that separates the internal network (LAN) from the external network (Internet). It usually hosts public-facing servers such as web servers, email servers, or FTP servers that need to be accessed by both internal and external users. A firewall is used to control the traffic between the DMZ and the LAN zones, and usually denies traffic from the DMZ to the LAN by default for security reasons. Therefore, if a web server in the DMZ needs to communicate with a file server in the LAN, it would need a special rule or permission from the firewall administrator. References: https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
NEW QUESTION 17
......
Thanks for reading the newest N10-008 exam dumps! We recommend you to try the PREMIUM Dumps-hub.com N10-008 dumps in VCE and PDF here: https://www.dumps-hub.com/N10-008-dumps.html (514 Q&As Dumps)